we are discontinuing the dplus content for now
Posts made by admin
-
RE: uNoGS dedicated site for Disney+ contentposted in Announcements
-
Add node back into galera cluster (brute force)posted in Blogs
Here is the scenario...
You have a 3 node galera (g1,g2,g3) cluster and there is some network maintenance which stops connectivity between the nodes causing them to lose their quorum and stop serving.
To fix this you disable 2 nodes (g2,g3) and bring just one back (g1)...
you should be able to bring the 1 node back with the following command:
galera_new_cluster
If that causes a failure, you may also need to update a line in your/var/lib/mysql/grastate.datfile.
to do this change:
safe_to_bootstrap: 0
to
safe_to_bootstrap: 1
now run thegalera_new_clustercommand again and it "should" work...Once your network settles down and connectivity is regained you will have 2 galera nodes which will no longer gracefully start up, what do you do?
Feel free to use the following hammer:
On g2
cd /var/lib/mysql rm grastate.dat rm ib_logfile* sudo -u mysql mysqld --wsrep_sst_donor=g1where "g1" is the wsrep_node_name of your working/primary galera node
follow the above instructions for g3 and you should be all set...
-
RE: Am I missing a different way to search?posted in General Discussion
@jamssyyy please let us know when you see a title that you believe does not exist in a country we are suggesting it is in... We update our library every 24 hours so it should be up to date.
-
uNoGS dedicated site for Disney+ contentposted in Announcements
Disney+ is now supported!
Over the last several months we have been putting together tools to pull title details for 45 Disney+ regions.Please visit https://dplus.uno.gs and have a look!
The good news about dplus is that for the moment vpn's such as nord work fine across regions so you should be able to view content in most of the countries we support!
enjoy!
-Admin
-
RE: Jumpcloud SSO (idp) to Keycloak (sp)posted in Blogs
Mapping Groups from Jumpcloud
In the above post we set up Jumpcloud SAML SSO auth to use Keycloak as the SP.
In addition, it is sometimes helpful to include your jumpcloud groups in the SAML token. The following instructions should help enable this.Configure Jumpcloud
- start by configuring your group to use the SSO App you created for SAML
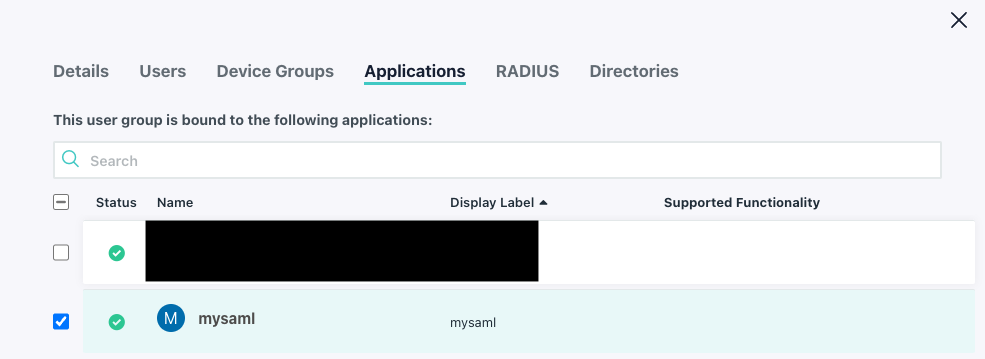
- Now update your SAML app to include group information:
- Go to your SSO App
- click on the SSO Tab and scroll to the bottom
- tick the box for
Group Attributes - give it a name like
memberOf(can be any name but you will need this for keycloak) - click
save
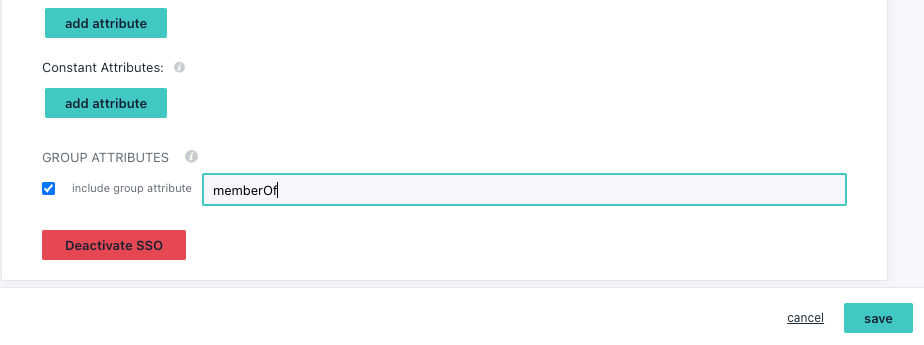
Configure Keycloak
- Open Keycloak admin portal for your realm
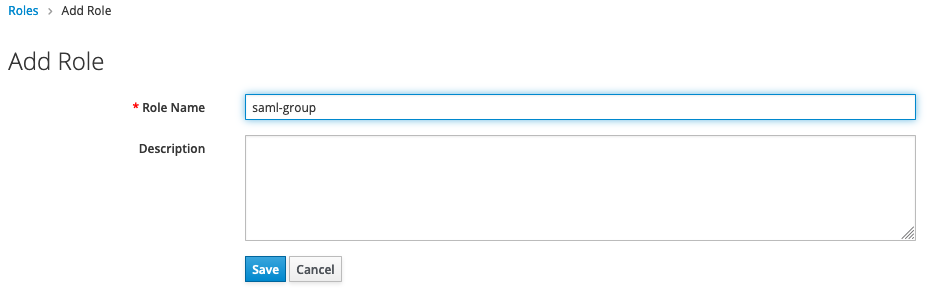
- Click on
Rolesand create a new role e.g.saml-group
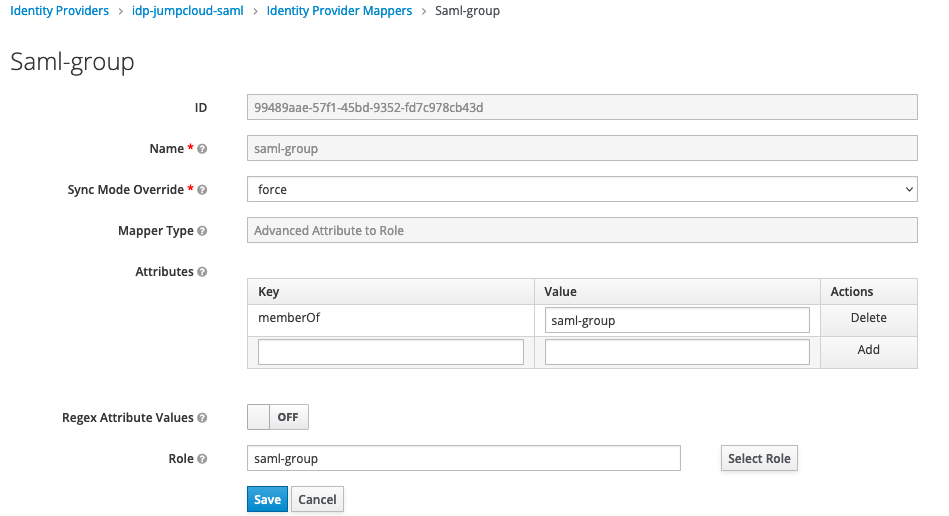
- Click on
Identity Providersand select the provider you created earlier (see above blog post) - Click on the
Mapperstab - Click
Create - Give it a name e.g.
saml-group - select
Sync Mode Overrrideequal toforce(this updates the groups associated with this account on every login) - Create a new
Attributesusing the JumpcloudGroup Attributesidentifier, in this casememberOfas the key and your Jumpcloud group name as the key - Set Regex Attribute Values to
On - Under Role, choose the role you created
-
Jumpcloud SSO (idp) to Keycloak (sp)posted in Blogs
Jumpcloud SAML SSO to Keycloak
So I recently had the challenge of setting up SAML authentication from Jumpcloud to an existing application that uses Keycloak (v18.x) as its authentication provider. As Keycloak can also be used as an identity provider the configuration can be a bit confusing.
Keep in mind this quick tutorial assumes that you already have an existing Keycloak client which you are using to authenticate your service. Details of building a client are outside the scope of these instructions.
So lets get into it...
Variables and Standards
The first thing we need to do is decide on some common variables and standards for this tutorial. Moving forward when referencing user defined variable we will wrap them in moustaches e.g.
{{var_here}}- iDpID:
idp-jumpcloud-saml(ID Provider ID) - BaseURL:
keycloak.example.com(base url of your Keycloak instance) - RealmName:
myrealm(Keycloak realm name) - RealmClient:
myclient - SPID:
sp-jumpcloud-saml(Service Provider ID) - AppID:
mysaml(Display label of your Jumpcloud App) - SPAppUrl:
https://unogs.com
Configure Jumpcloud
- Login to the Jumpcloud admin interface
- Click on
SSO - Click the large green
+button - Click
Custom SAML App(bottom of page) - Fill out your display label with
{{JDSID}} - Fill in a description if you want
- Click on the
SSOTab - fill in
IdP Entity IDwith{{iDpID}} - fill in
SP Entity IDwith{{SPID}} - fill in
ACS URL:https://{{BaseURL}}/realms/{{RealmName}}/broker/{{iDpID}}/endpoint - select
SAMLSubjectNameID:asusername
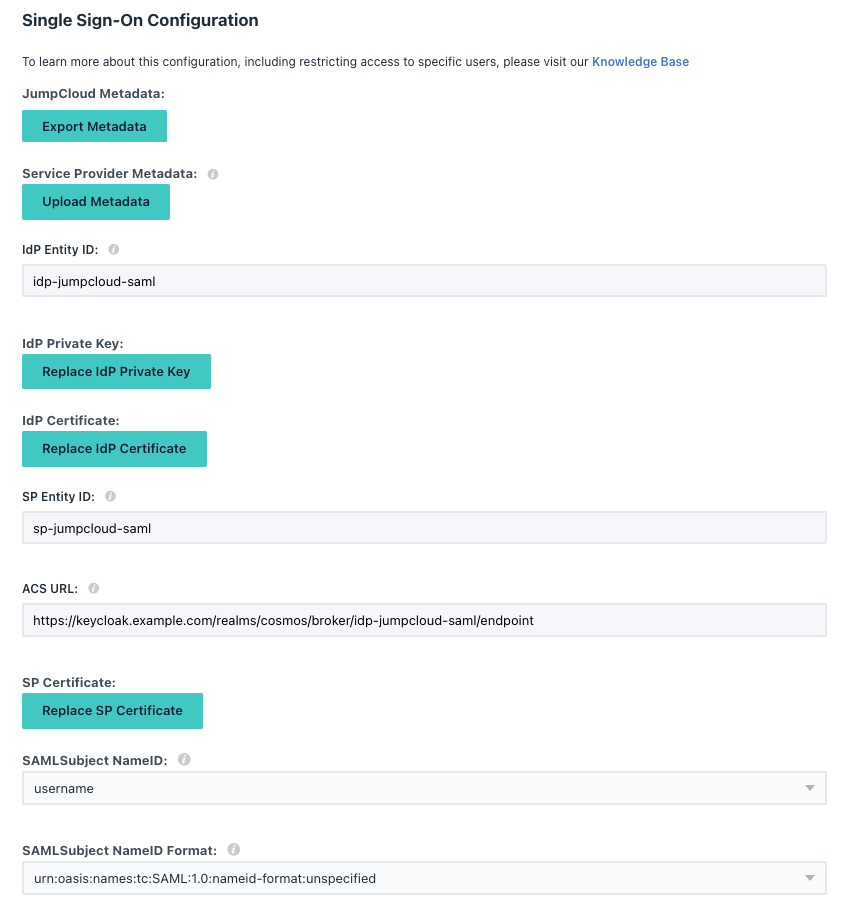
- select
Signature AlgorithmasRSA-SHA256 - fil in
Login URLashttps://{{BaseURL}}/realms/{{RealmName}}/protocol/openid-connect/auth?response_type=code&client_id={{RealmClient}}&scope=openid&redirect_uri={{SPAppURL}}&kc_idp_hint={{SPID}}- note: if you want to see your previous keycloak login screen remove:
kc_idp_hint
- note: if you want to see your previous keycloak login screen remove:
- tick
Sign Assertion - fill in
IDP URLwith{{APPID}} - Add the following
User Attributes:- value
emailselectemail - value
firstnameselectfirstname - value
lastnameselectlastname
- value
- e.g.
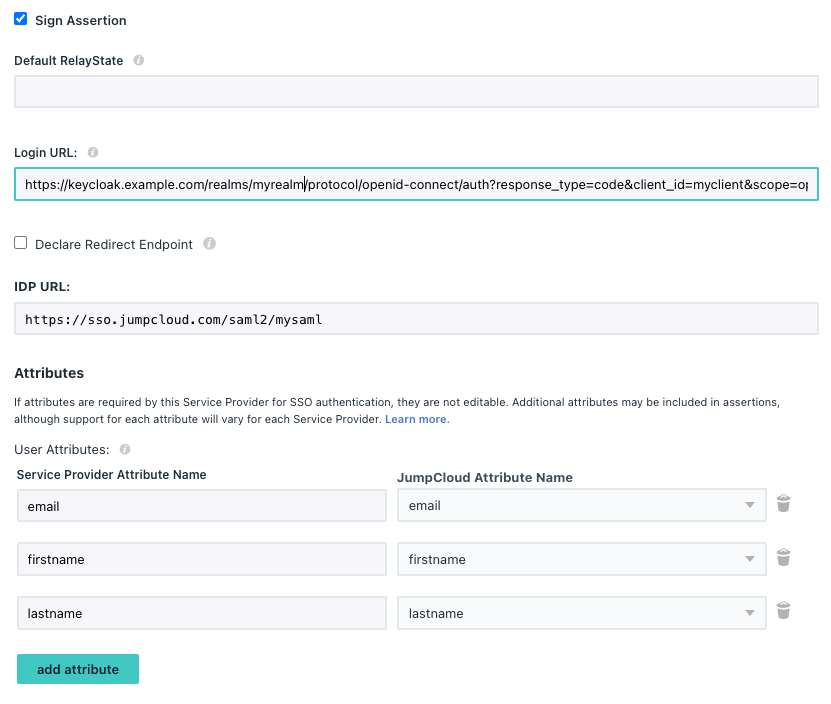
- click
activate - click on your newly created APP
- click on the
User Groupstab and select the group you want to give the above app access to. - click on the
SSOtab - click
Export Metadata, an xml calledJumpCloud-saml.xmlfile will be saved locally
Configure Keycloak
Via the admin portal:
- click
Identity Providers - select
Add Providerand selectSAML v2.0 - change
Aliasto{{iDpID}} - e.g.
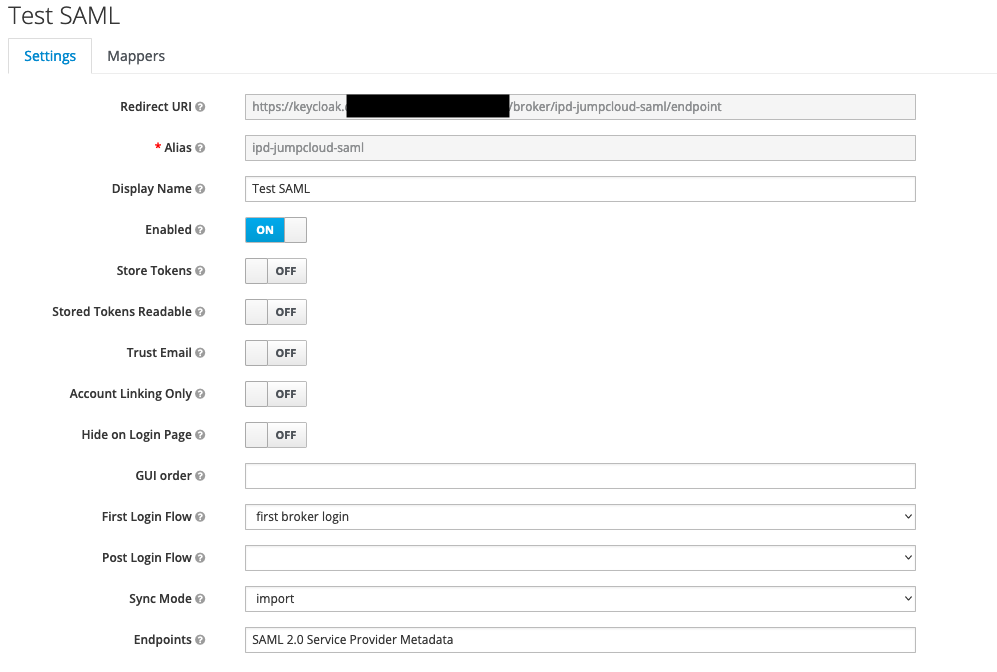
- change
Service Provider Entity IDto{{SPID}} - scroll to bottom of the page, select
Select Fileand chooseJumpCloud-saml.xml - click
Import - click
Save - e.g.
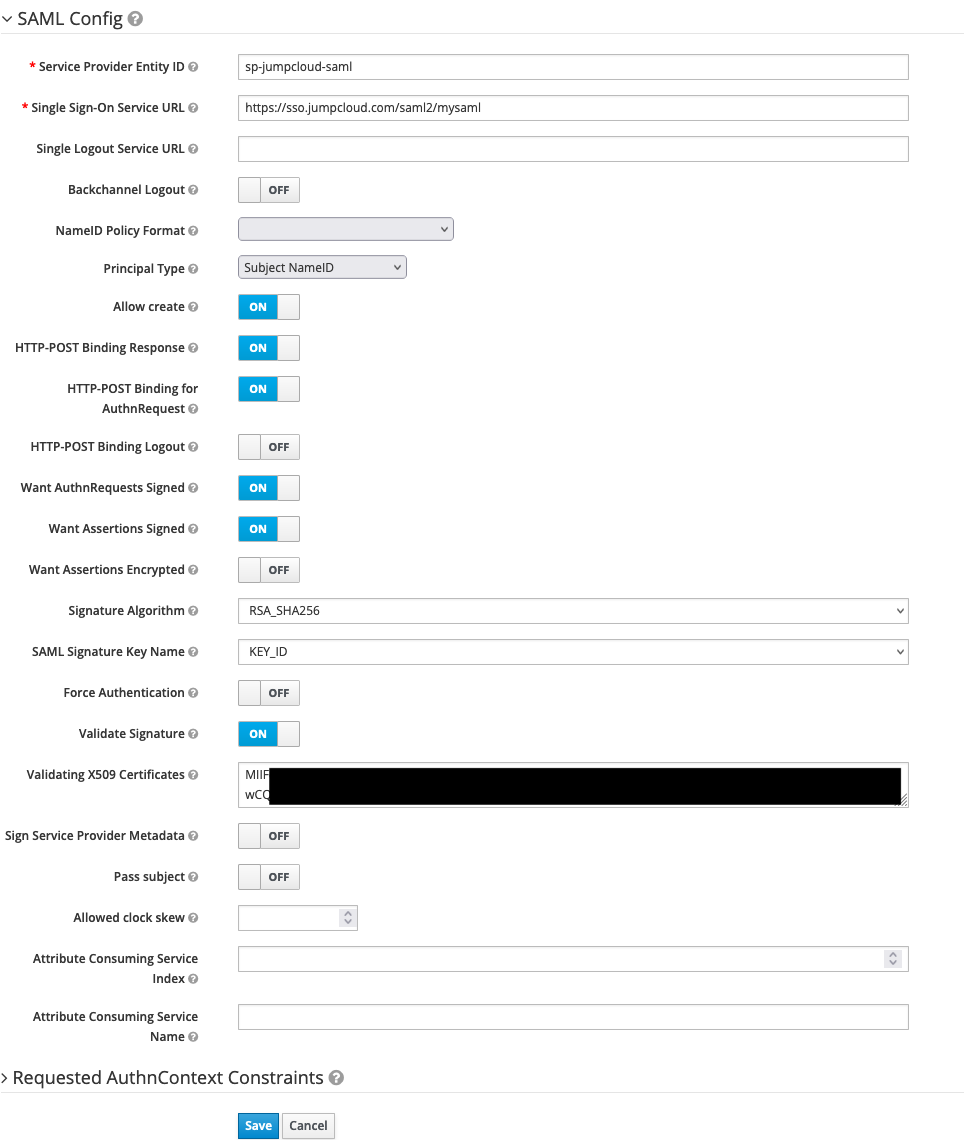
- go back into newly created provider and click the
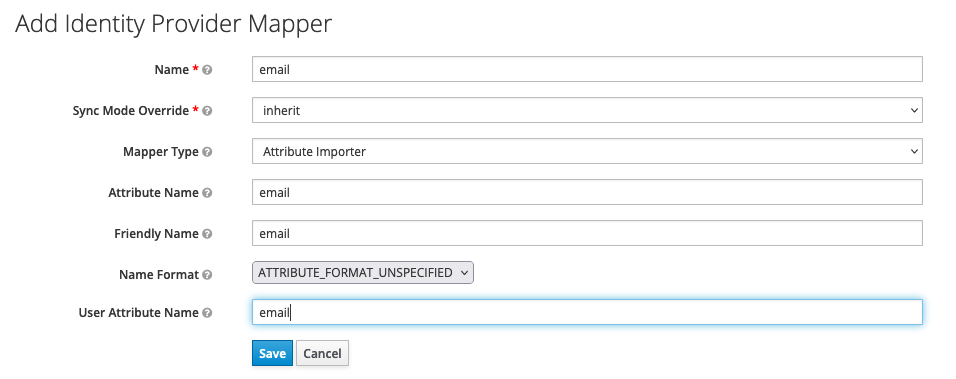
Mapperstab - do the following for email, firstname and lastname
- click
create - give it a name
- change Mapper type to attribute importer
- fill in
Attribute Nameto type (email, firstname, lastname) - fill in
Friendly Nameto type (email, firstname, lastname) - select
ATTRIBUTE_FORMAT_UNSPECIFIED - fill in
User Attribute Namekctype (email,firstName,lastName)
- click
Wrap UP
If everything went as planned, the above configuration should allow your users to click on a new app in their jumpcloud console and it will automatically login via your existing client. For new users this configuration should also automatically populate user details in the JWT.
If you have any questions or anything doesn't work as expected feel free to email me at admin@unogs.com
- iDpID:
-
RE: Need access to a database for school projectposted in Comments & Feedback
https://rapidapi.com/unogs/api/unogs/ this requires some basic experience with web API's but will provide all the information you need... there is a free daily quota but it does require a credit card.
-
RE: Episode translation to IMDb IDposted in Netflix API Details
we do not currently support IMDB on individual episodes..
-
RE: How to get the latest images from a title? Looks like the API hasn't been updated with the new onesposted in Netflix API Details
we will look into this and let you know
-
RE: Hong Kong region in Country Details not updatingposted in Comments & Feedback
we are updating hong kong as I see new regional titles... netflix may have changed there expiring data...
-
Take advantage of our partnership with PureVPN!posted in Announcements
All,
We have recently started working directly with PureVPN in order to offer the best VPN experience for watching Netflix.
If you want to support uNoGS and need a great VPN provider please click on the link below and use the offer code
unogs20to get an additional 20% off your purchase!Click Here to Check out PureVPN
Kind Regards
-Admin
-
RE: can't play videosposted in Comments & Feedback
Netflix are constantly evolving their restrictions unfortunately, you just need to work with your VPN provider as they sort things out.
-
RE: Am I missing a different way to search?posted in General Discussion
definitely the VPN's being blocked... little we can do about it until the VPN companies find a work-around
-
RE: Hong Kong region in Country Details not updatingposted in Comments & Feedback
we are looking into it, thanks for letting us know
-
RE: Netflix is Blocking some Residential Addressesposted in Announcements
Update: We have found a work-around and all 38 countries are now back... we will update this Announcement if anything changes...
-
Netflix is Blocking some Residential Addressesposted in Announcements
All,
Over the past few weeks it has become apparent that Netflix has once again launched a campaign to block 'certain' IP addresses from accessing all 'non-original' content. You will know this happening to you if you suddenly see a drastic reduction in available content.
More information:
- https://arstechnica.com/gadgets/2021/08/netflix-is-adding-residential-ip-addresses-to-its-vpn-blocklists/
- https://torrentfreak.com/netflix-intensifies-vpn-ban-and-targets-residential-ip-addresses-too-210811/
- https://www.makeuseof.com/netflix-starts-limiting-what-vpn-users-can-watch/
As a provider of what Netflix is showing in each country, this crack-down has affected uNoGS ability accurately update information in certain countries. As of today we have stopped providing information for the following countries:
- Belgium
- Czech Republic
- Hungary
- Spain
- Ukraine
We are currently looking for valid alternatives for these issues and will let everyone know once we find a work around. Sorry for any inconvenience.
If you have any suggestions or additional information on this crack-down please let us know in comments below.
Thanks!
